Security Through Obscurity: Hiding WordPress from Bad Robots
WordPress is probably the most popular website framework on the planet Earth.
In the security community it is also known as one of the most exploitable frameworks for a number of reasons.
There are pretty much 2 main types of WordPress attacks that I’ve been seeing these days, nothing new:
- Brute forcing wp-admin via dictionary attack.
- Injecting code /payload shell via MYSQL injection attack mainly due to outdate plugins or framework version
Outside of that there are some more targeted types of attacks, but these are the main ones.
Today’ I’ll be talking briefly about WordPress brute force style attacks. To give you just a little idea of how ridiculously common these attacks are, take a look at these logs from a very small website that I administer:
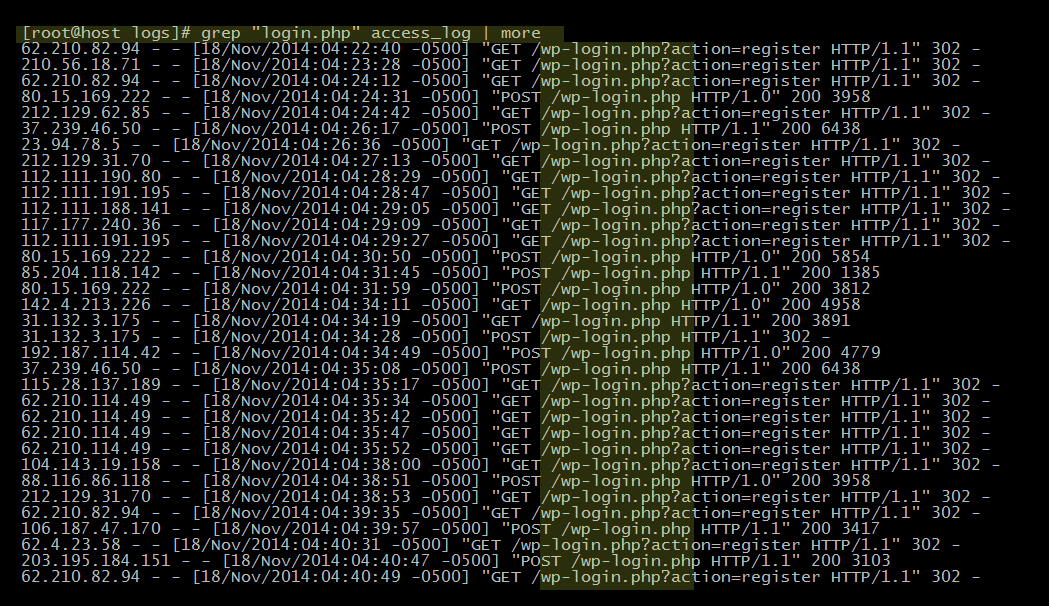
Crazy right? Well that is just a piece of the pie. Let’s allow grep to dump all attempts from November 18th till tonight, December 1st –
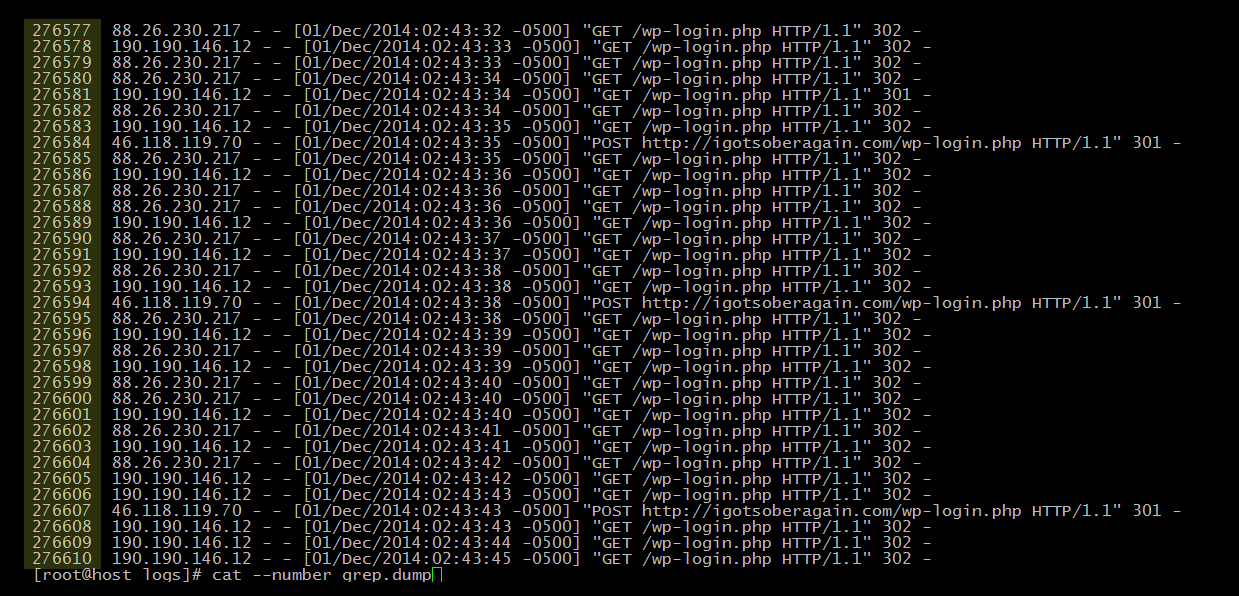
See that first column? That is the line number or essentially the number of login attempts in about 2 weeks.
Over 270,000 dictionary attack attempts in about 2 weeks!
Remember, this is an extremely small site that I admin, and it gets under 50 visitors per day.
Can you imagine how many attempts a larger site might get?
Lock it down
If this sounds familiar to you, you might want to think about hiding WordPress from the rest of the world. Now, there are a few schools of thought on hiding the wp-admin folder or login page.
- password protecting the folder using Apache config or .htaccess
- restricting the login to a specific IP addresses
- restricting the login from a specific referrer
- renaming the login page
There are also dozens of other ways to “hide” WordPress from bots, but this method is probably the most instrumental in preventing brute force, which seems to be the most common.
The method I’ve personally used in the past is restrict access to wp-admin and login.php to my IP addresses. Luckily I have a static IP address on both of my work locations and VPS, so I don’t have to worry about dynamic IP’s.
So it is pretty simple from here, just a basic .htaccess edit. You are basically telling Apache “only allow this IP(s) to access these files or folders.”
This is something you could implement server wide if you wanted to, but if you have multiple clients with multiple IP addresses that is where it really starts to get tricky.
Throw this in your .htaccess
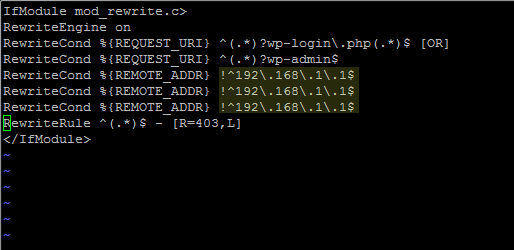
Obviously change 192.168.1.1 to your IP(s). Feel free to append as many lines as you like.
Blocking IPs
My personal policy on blocking IP addresses is this: if an IP makes failed attempts a few times, it won’t get blocked however if it persistently hits the server day after day it gets blocked.
Keep in mind most of this brute forcing is done via VPS > proxy server so many attackers will easily be able to rotate through hundreds of IP addresses in a given session.
If you do want to block an IP address I strongly encourge you to do so in your Apache config / access control. If you don’t have access to that or are on a shared server you can do so in the .htaccess file.
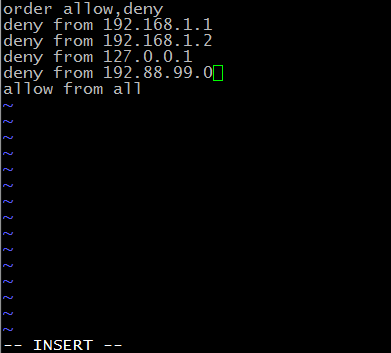
A more savvy admin will create a bash or PHP / python script to automatically parse and append these IP addresses to the .htaccess. I’m currently looking into this right now but have a few issues I haven’t worked out yet, mainly implementing my policy. There is an excellent thread at stack overflow on automagically blocking IP’s via script in Apache.
Finally a word of caution: while I have been an amateur Linux admin for about 20 years, I am in fact still an amateur. It is not something I do professionally so use all of this at your own risk!
If you have any questions please feel free to hit me up on Twitter.



